What is end-to-end encryption and how does it work?

End-to-end encryption is the most secure approach to convey secretly and safely on the web. By scrambling messages at the two parts of the bargains, end-to-end encryption keeps anybody in the center from perusing private correspondences.
As of not long ago, end-to-end encryption (E2EE) was the sole space of the well informed in light of the confounded tasks required to utilize it. Be that as it may, later innovative advances have made end-to-end encryption a lot simpler to utilize and increasingly available. Right now, will disclose what is end-to-end encryption and what points of interest it offers over standard encryption.
What is end-to-end encryption (E2EE)?
At the point when you use E2EE to send an email or a message to somebody, nobody observing the system can see the substance of your message — not programmers, not the administration, and not by any means the organization (e.g., FIREFILE.CC) that encourages your correspondence.
This contrasts from the encryption that most organizations as of now use, which just ensures the information in travel between your gadget and the organization’s servers. For instance, when you send and get an email utilizing a help that doesn’t give E2EE, for example, Gmail or Hotmail, the organization can get to the substance of your messages since they likewise hold the encryption keys. E2EE kills this probability in light of the fact that the specialist co-op doesn’t really have the unscrambling key. Along these lines, E2EE is a lot more grounded than standard encryption.
How does end-to-end encryption work?
To see how E2EE functions, it assists with taking a gander at an outline. In the model beneath, Bob needs to make proper acquaintance with Alice in private. Alice has an open key and a private key, which are two numerically related encryption keys. The open key can be imparted to anybody, however just Alice has the private key.
In the first place, Bob utilizes Alice’s open key to encode the message, turning “Hi Alice” into something many refer to as ciphertext — mixed, apparently irregular characters.
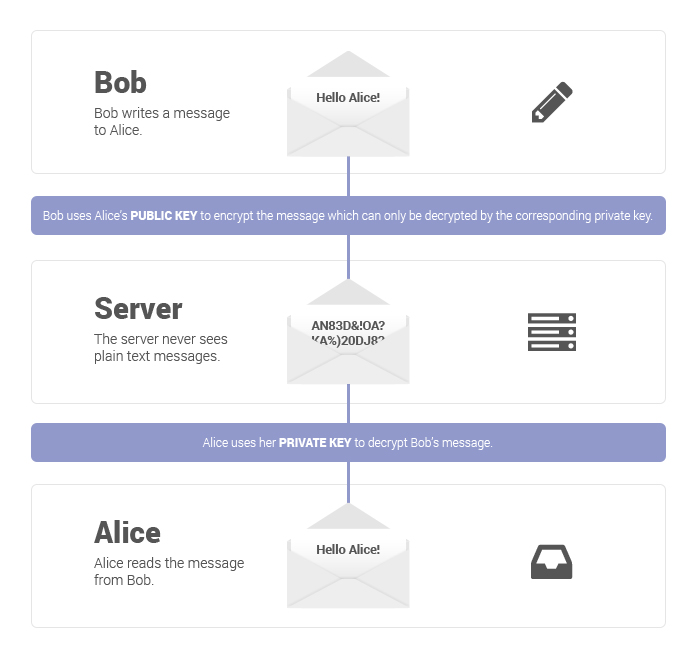
Weave sends this scrambled message over the open web. En route, it might go through various servers, including those having a place with the email administration they’re utilizing and to their network access suppliers. In spite of the fact that those organizations may attempt to peruse the message (or even offer them with outsiders), it is inconceivable for them to change over the ciphertext once again into lucid plaintext. No one but Alice can do that with her private key when it arrives in her inbox, as Alice is the main individual that approaches her private key. At the point when Alice needs to answer, she essentially rehashes the procedure, encoding her message to Bob utilizing Bob’s open key.
Favorable circumstances of end-to-end encryption services
There are a few points of interest of E2EE over the standard encryption that most services use:
-
It protects your information from hacks. E2EE implies less gatherings approach your decoded information. Regardless of whether programmers bargain the servers where your information is put away (e.g., the Yahoo mail hack), they can’t unscramble your information since they don’t have the decoding keys.
-
It keeps your information private. On the off chance that you use Gmail, Google can know each personal detail you put in your messages, and it can spare your messages regardless of whether you erase them. E2EE gives you power over who peruses your messages.
-
It’s useful for popular government. Everybody has the privilege to security. E2EE ensures free discourse and shields aggrieved activists, dissenters, and columnists from terrorizing.